Maxim Afanasiev
Since 1997, Kerio Technologies has been developing and releasing unique software solutions in the field of computer security to protect internal company networks from external attacks and creates systems for collaboration and electronic communications. Products from Kerio Technologies are aimed at medium and small businesses, but can also be successfully used in large companies. It is worth noting that the software is developed taking into account global trends in the field of information security, and the company itself is an innovator in this area.
Prototype software package The Kerio Control discussed in this article was the Winroute Pro software gateway, the first version of which was released in 1997. Winroute Pro software was an advanced proxy server designed to provide access local computers to the Internet through one external Internet channel. This product almost immediately gained popularity and quickly became a competitor to one of the most widespread proxy servers at that time, WinGate. Even then, Kerio products were distinguished by a clear interface and convenient configuration, and also, importantly, reliability and security. Since then, Kerio Winroute has been constantly modernized, many useful functions and opportunities. At the beginning of its journey it was called Winroute Pro, then the name was changed to Winroute Firewall, and starting from version 7 the product received its current name - Kerio Control.
Kerio quickly realized the possibilities of virtualization and took the path of maximum integration with virtual environments, which today are actively developing thanks to the emergence of multi-core processors and significant progress in the IT field. All new Kerio products are now available for VMware and Hyper-V virtualization environments, allowing you to deploy the software on any platform and migrate the product without having to reinstall it on a new hardware platform. In addition, this approach offers company network administrators greater choice when building their network infrastructure. Kerio products were originally delivered as Windows applications, but after the release of the version for virtualization systems, the company decided to completely abstract from the operating system and no longer release Kerio Control as a separate application. Starting with version 8, Kerio Control comes in only three flavors: Software Appliance, VMware Virtual Appliance and Hyper-V Virtual Appliance. All options use a modernized operating room Linux system based on Debian (using the SMP version with reduced functionality), which does not require additional lengthy setup and maintenance. The Firewall Software Appliance is available as an ISO image just over 250 MB in size and can be easily installed on dedicated hardware without requiring an operating system installation. VMware Virtual Appliance comes in OVF and VMX packages for VMware environments, and Hyper-V Virtual Appliance is designed for Microsoft virtualization systems, all pre-deployed with configurable options. According to the developer, the OVF version of this software, in principle, can be installed on other virtualization systems. This approach allows a more flexible approach to the implementation of a company’s network and abandons the use of hardware solutions, which often cannot be upgraded in hardware, since this requires significant costs, or their capabilities are strictly limited.
Let's look at the main features of the Kerio Control software, as well as a number of innovations that were missing in previous versions. Let us remind you that the 8th version of Kerio Control was first released in March of this year. At the time of writing, in addition to a small update, Kerio released the Kerio Control 8.1 update in June, which also brought some additional functionality.
Installation of Kerio Control can be done either using Software Appliance, that is, deploying the system from a separate ISO image, or by initializing a virtual machine on a virtualization server. Last method suggests several installation paths, including the possibility automatic download the latest version of Kerio Control from the manufacturer's website through the Vmware VA Marketplace. When installing from an ISO image, all steps to deploy Kerio Control involve the administrator answering a few simple questions from the installation wizard. Initializing the Kerio Control virtual machine allows you to skip the main installation stage, and the administrator only needs to set the initial parameters of the virtual machine: number of processors, volume RAM, number of network adapters and size disk subsystem. IN basic version virtual machine Kerio Control has the most minimal parameters, however, to perform further administration you need at least one network adapter specified in the machine properties.
After installing the system in one way or another and successfully initializing Kerio Control, the user will have access to basic setup network configuration via the management console (Fig. 1). Default network adapters connected to Kerio Control attempt to obtain IP addresses using DHCP. If obtaining IP addresses was successful, the administrator can connect to Kerio Control via the local network by entering the IP address displayed in the management console. Basic console controls allows you to configure network settings adapters, reset Kerio Control to basic settings, reboot or turn off Kerio Control. It is worth noting that, if necessary, you can exit to the full bash command shell of the operating system by pressing the Alt + F2-F3 key combination. To log in, you will need to enter the root login and administrator password specified when installing Kerio Control. Additional debugging information can be called up by pressing Alt + F4-F5. Further customization settings occurs through the web administration console over an SSL encrypted channel.
Rice. 1. Management console
All parameters can be set via the control panel, which operates through a secure web interface (Fig. 2). Work with such an interface is carried out through the secure HTTPS/SSL protocol. The administration console allows you to manage all firewall settings. Compared to previous versions based on version 7 of Kerio Control, the design of this control panel has undergone significant changes. Thus, the first page of the control panel has a tiled, customizable interface (“Dashboard”), to which you can add or remove the necessary elements for quickly diagnosing the status of Kerio Control. This is very convenient, since the administrator immediately sees the load on communication channels, user activity, system status, VPN connections, etc.
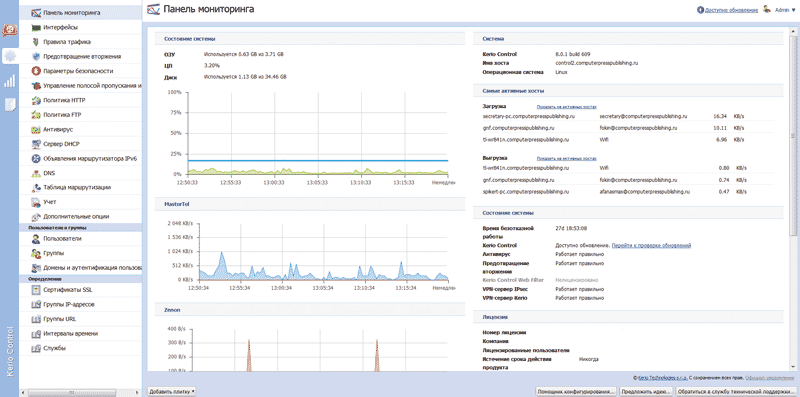
Rice. 2. Control panel
The following options have been added to the updated version of Kerio Control 8.1: saving configuration and settings in cloud service Samepage.io in automatic mode, monitoring parameters via the SNMP protocol, the ability to use debugging tools Ping, Traceroute, DNS Lookup, Whois on behalf of the Kerio Control gateway in the administration web interface. In addition, Kerio Control now supports regular expressions for URLs, automatic raising of VPN tunnels, password brute force protection and more advanced packet analysis capabilities. It should also be noted that the latest version of Kerio Control Software Appliance adds support more RAID controllers, which will expand the possibilities for deploying this system on individual hardware platforms.
The Kerio Control web management interface has not only an administrative panel, but also a separate user interface(Fig. 3). The administration panel does not have the ability to change anything in Kerio Control, but allows you to track user or user statistics over various periods of time. Statistics provide data on resources visited, the amount of data transferred and other information. If a user has an administrative account in the Kerio Control system, he can receive statistical data about other users of the system through this control panel. Accurate and well-thought-out statistics help the administrator to find out user preferences when working on the Internet, find critical elements and problems. The panel generates a detailed histogram of traffic usage for each user on the network. The administrator can select the period for which he wants to track traffic usage: two hours, a day, a week and a month. In addition, Kerio Control shows statistics on actual traffic usage by type: HTTP, FTP, email, streaming multimedia protocols, data exchange directly between computers or proxies.

Rice. 3. User panel
For a modern company, whose branches may be located all over the world, a secure connection to the corporate network is a necessary condition, since outsourcing is actively developed today. Using Kerio Control, installing virtual private network requires virtually no effort. The VPN server and clients are part of Kerio Control's secure remote access to the corporate network. Usage virtual network Kerio VPN allows users to remotely connect to any resources on the corporate network and work with the organization's network as if it were their own local network. Built into the Kerio Control product VPN server allows you to organize VPN networks according to two different scenarios: “server - server” and “client - server” (used by Kerio VPN Client for Windows, Mac and Linux). The “server to server” mode is used by companies that want to connect a remote office via a secure channel for sharing shared resources. This scenario requires Kerio Control on each of the connecting sides to establish a secure channel over open network Internet. The "client-server" mode allows a remote user to securely connect a laptop or home computer. As many system administrators know, the VPN and NAT protocols (translation network addresses) do not always support collaboration. Kerio VPN is designed to reliable operation through NAT and even through a series of NAT gateways. Kerio VPN uses standard SSL channel control (TCP) and Blowfish (UDP) encryption algorithms, and also supports IPSec.
Kerio Control Gateway has built-in virus protection, which is provided by scanning both incoming and outgoing traffic. If previously Kerio Control used a built-in antivirus from McAfee, then now latest versions Sophos antivirus is used. The administrator can set inspection rules for traffic over various protocols: SMTP and POP3, WEB (HTTP) and file transfer (FTP). The firewall's built-in antivirus installed on the gateway provides complete protection for traffic passing through the gateway. Since the integrated antivirus can receive updates with new virus databases in real time, this significantly increases the level of network security, along with the use of antivirus programs on every computer on the local network. The antivirus scans incoming and outgoing messages, as well as all attachments. If a virus is detected in an attachment, the entire attachment is deleted and a notification is added to the email. In addition, Kerio Control scans all network traffic, including HTML pages, for embedded viruses. Files downloaded via HTTP and files transferred via FTP are also scanned for viruses. Additionally, it should be noted that for organizations and institutions such as schools that do not want their employees and clients to visit certain pages, Kerio Control with the built-in Kerio Control Web Filter (available as an option at an additional cost) provides additional features on blocking pages on the Internet.
Kerio Control allows administrators not only to create an overall traffic strategy, but also to set and enforce restrictions for each user. Each user must log in to Kerio Control before accessing the Internet. Accounts users are stored in a separate internal base user data or taken from the Microsoft corporate database Active Directory or Apple Open Directory. Maybe parallel use both local and domain user databases. When using integration with Microsoft Active Directory, client authorization can occur transparently for domain users through NTLM authentication. As part of Windows 2008/2012 Server, Active Directory allows administrators to centrally manage user accounts and network resource data. Active Directory provides access to user information from a single computer. Active Directory/Open Directory support gives Kerio Control access to the user database in real time and allows you to set up a user on the local network without saving a password. This way, there is no need to sync passwords for each user. All changes in Microsoft Active Directory/Open Directory are automatically reflected in Kerio Control.
The administrator can set different access rights restrictions for each user. These rules can be set to operate for specific periods of time and set various restrictions on traffic usage. When the limit is reached, Kerio Control sends an email warning to the user and administrator, or the administrator blocks that user for the rest of the day or month.
In conclusion, it is worth noting that Kerio Control is a very popular product among system administrators due to its undeniable advantages that it has compared, for example, with similar solutions included in the standard package operating systems Linux-based (for example, iptables). Quick setup, ample opportunities and a high degree of protection - all this is done by this software product attractive for small companies.
Let's start setting up the security of our UTM gateway on the Kerio Control 7.4.1 platform
First of all, let's move on to setting up the IDS/IPS system and set the update schedule to 1 hour instead of the default 24 hours. The update does not “load” the device at all, but it significantly increases the chances of catching the malware.
Now let’s set the actions, for High severity “Log and delete”, for Medium “Log and delete”, for Low severity “Log”:
Such settings can significantly affect the “normal” operation of “problem” PCs, which is what we are about to hear through the Help Desk and see in the Security Magazine:
Well now go to the “Security Settings” section and allow access to the local network via MAC address only to the listed computers, for this we will prepare a list in advance MAC addresses that are used in the organization.
When adding a new device to the network, we will add its MAC, this is inconvenient and therefore it is logical to entrust this to the Help Desk service. But in this case, they will have to allocate administrative rights to UTM, which is unacceptable because destroys any security :)
Someday Kerio will use RBAC in its products, but for now we will select a guest network for guests of the organization and will not filter by MAC there.
Go to the “Miscellaneous” subsection and increase the connection limit per host to 6000. This may be necessary for all sorts of applications such as client banks, etc.
Let’s also make sure that the anti-spoofing module is enabled and events are recorded in the log:
Let's move on to the "HTTP Policy" section and first of all, enable "Remove advertisement and banners", and for debugging purposes, enable logging of this rule.
Now, taking into account the possibility of leaking information through social networks, we will prohibit their use; to do this, we will create a new rule “Social”, select the action “Refuse”, enter the text “ According to policy information security usage social networks forbidden.", but since in our case this is not a ban, but rather a recommendation, we will enable the ability for users to unblock this rule.
As a URL, we will not list all sorts of http://vk.com and https://facebook.com, but will indicate a URL rated by the Kerio Control Web Filter rating system (and of course we will filter including https).
Our rule will be valid for all users, at any time, and events will be recorded in the Log.
In real conditions, it most often happens that a prohibiting rule is created for all users. working hours with the exception of lunch (i.e. in the morning, at lunch and after work, your favorite VKontakte will work).
And for the VIP group (which may include managers, top executives and other privileged employees) access will be denied at any time, but with the possibility of unblocking.
I will leave this Customer’s decision without comment, I’ll just show you what it looks like:
In a similar way, you can manage all Internet traffic very flexibly, because Kerio Web Filter is amazingly good.
I don’t use forbidden words, I leave the settings at default, but in the Kerio Control Web Filter settings I will allow users to report suspected errors, because all systems are imperfect in their own way, and Habr’s blocking “out of the box” is proof of this:
As for FTP filtering, users practically do not use it, so I will include only two standard rules and will not write my own until incidents occur:
Let's move on to the Antivirus settings. First of all, let's set the update schedule to one hour, because... practice suggests that signatures are updated more often than 8 hours.
Because protect email At the gateway level, I don’t think it’s a very good idea, I’ll disable SMTP and POP3 scanning, I’ll also disable FTP because practice suggests that this protocol is used more often by administrators, and users have already successfully forgotten about it.
And on the “Email Scanning” tab. mail”, just in case, I will allow the transfer of attachments, even if they were somehow mistaken for malicious.
Of course, in terms of security monitoring the most important condition, so let's configure Kerio Star according to your needs.
In order to reduce the administrative burden, we will set up exceptions for some traffic and for VIP employees, to whose traffic even system administrators should not have access:
In the “System Access” subsection, we will allow users access to their own statistics, and moreover, we will automatically send them these same statistics weekly.
For some responsible person (in this case, this person is me) it is possible to access and receive daily reports on the activities of all employees.
Also, the system administrator has the opportunity to receive notifications about the following system events:
Of course, for all these functions to work properly, Kerio Control must have an SMTP relay configured, and a valid email must be specified in each user’s profile.
In the Additional Options, in the “P2P Limiter” subsection, you can block torrets that are likely to be harmful on the corporate network.
In this case, the user will be notified by email (the administrator can also be notified by email) and blocked for 20 minutes.
UPD It is possible to disable Java, ActiveX, etc. both for individual users and for the entire organization:
And of course, regularly review all the magazines; I’ll tell you how to make this process convenient next time.
About studying the products of Kerio Technologies, which produces various security software solutions for small and medium-sized businesses. According to the company's official website, its products are used by more than 60,000 companies around the world.
SEC Consult specialists discovered many vulnerabilities in Kerio Control, the company's UTM solution, which combines the functions of a firewall, router, IDS/IPS, gateway antivirus, VPN, and so on. The researchers described two attack scenarios that allow an attacker not only to seize control of Kerio Control, but also of corporate network which the product is intended to protect. Although the developers have already released fixes for most of the detected bugs, the researchers note that it is still possible to implement one of the attack scenarios.
According to researchers, Kerio Control solutions are vulnerable due to unsafe use PHP functions unserialize and also due to the use old version PHP (5.2.13), which has previously been found to have serious problems. Experts also discovered a number of vulnerable PHP scripts that allow XSS and CSRF attacks and bypass ASLR protection. In addition, according to SEC Consult, the web server runs with root privileges and has no protection against brute force attacks and memory corruption.
Diagram of the first attack scenario
The first attack scenario described by experts involves the exploitation of several vulnerabilities at once. The attacker will need to use social engineering and lure the victim to a malicious site that will host a script that will allow them to find out the internal IP address of Kerio Control. The attacker must then exploit the CSRF bug. If the victim is not logged into the Kerio Control control panel, the attacker can use regular brute force to select credentials. This would require an XSS vulnerability to bypass SOP protection. After this, you can move on to bypassing ASLR and take advantage of an old bug in PHP (CVE-2014-3515) to launch a shell with root rights. Essentially, the attacker then gains full access to the organization's network. The video below shows the attack in action.
The second attack scenario involves exploiting an RCE vulnerability, which is associated with the Kerio Control update function and was discovered more than a year ago by one of the SEC Consult employees. Experts suggest using this bug, which allows remote execution of arbitrary code, in combination with an XSS vulnerability, which allows expanding the functionality of the attack.
Kerio Technologies specialists were notified of the problems at the end of August 2016. On at the moment the company released Kerio Control 9.1.3, where most of the vulnerabilities were eliminated. However, the company decided to leave root privileges to the web server, and the RCE bug associated with the update function still remains without a fix.
Many people use the Kerio Control firewall. It has the widest functionality, reliability and ease of use. Today we’ll talk about how to set up bandwidth management rules. Simply put, let's try to limit the speed of Internet access for users and groups.
How to limit Internet speed for users and groups in Kerio Control
And so let’s go to the Kerio Control administration panel. On the left we look for the item Bandwidth Management. First, let's indicate the speed of your Internet connection. At the bottom, in the Internet connection bandwidth field, click change and enter the speed for downloading and uploading. This data is needed for correct operation Kerio Control itself.
Now add a new rule, click add and enter a name.

Next, in the Traffic field, you need to indicate for whom this restriction will apply. There are a lot of options, but we are interested in specific groups and users, so click on Users and groups. In the window that opens, select the required users or group. You can immediately select both the group and users.

Now set the download speed limit. We indicate how much of the total speed needs to be reserved for these groups and users and the limit itself. We indicate the same for the download item.

We leave the interface and available time as default and apply this rule.
Good afternoon, dear readers and guests of the blog site, in any organization there are always people who do not want to work and who use corporate resources for other purposes, I will give a simple example: you have a small office, let’s say 50 employees and an Internet channel with throughput 20 megabits and a monthly traffic limit of 50 GB, for normal use The Internet and building business work is enough for the office, but there are people who may want to download a movie for the evening or a new music album, and most often they use terrent trackers for this, let me show you how in Kerio Control 8 you can prohibit p2p traffic and set a daily traffic limit for the employee.
Blocking p2p traffic in Kerio Control 8
And so you have built a local network in which a malicious downloader has appeared, I think you will identify it immediately from the statistics logs, filter it by columns. Apart from the reprimand that will follow from the management, you are like system administrator should prevent further attempts to download content via p2p traffic.

You have two options:
- Enable complete blocking of p2p traffic
- Set a daily limit per user
Let's start by blocking peer-to-peer traffic, go to the content filter and create a new rule. Click add and select "Applications and web content categories"

Find the download section and check the peer-to-peer network checkbox.

In action, set the rules to delete.

In theory, to completely block p2p traffic, a created rule is enough, but I also advise you to set quotas for users if you have an Internet limit, in order to teach them to use it exclusively for work matters. To do this, go to the Users tab and in the properties of any on the "Quota" tab, specify the daily limit in megabytes.